What is Social Engineering?
In cyber security, social engineering is a process of making our target take some action that they won’t do usually. In social engineering, we combine the use of human manipulation techniques and technical deceiving techniques. Here we don’t put guns to our target’s heads and ask them to do what we want. We just create some scenarios that are misunderstood by the target, and that’s how we make them do what we want.
Why You should learn Social Engineering?
In cyber security, the biggest threat of all is human manipulation. Imagine using a million dollars in your corporation’s security to prevent malicious actors from getting inside. But you have employees who just got manipulated by the attacker to install something malicious into your system. What will happen? Simple your system will be compromised despite all your investment.
The most effective defense you can use to defend against social engineering attacks is to learn about this and create awareness. We will explain how to avoid attackers’ traps later in this article.
Two main parts of Social Engineering
Social Engineering has two core parts. 1. Human part, 2. Technical part.
Human part
No matter how perfectly the attacker covered their malicious code. If the attacker is unable to manipulate the target to execute their malicious code, it all becomes useless. The most successful ratio in social engineering depends on human manipulation (human part).
Technical Part
This is the part where the attacker crafts malicious payloads. That’s going to give him access to their target’s system. The success of this part depends on the success of the human part.
Types of social engineering attack
There are different types of social engineering techniques. But those are the top 3 methods of social engineering. They are:
Phishing
Phishing is the most common and most dangerous hacking technique available. No matter how better the defense system you are using, phishing will breakthrough all of the defenses. In phishing, the attacker manipulates the target to click a link and download some malicious software. The attacker creates the phishing message in a way that looks original and genuine. And the attacker also uses some techniques which doesn’t allow the victim to think much.
Smishing
This is just like phishing, but this attack happens using SMS. Here the attacker crafts a message inserts malicious links and manipulates the target to click on the link. Or another way the attacker asks for information from the victim.
Pretexting
In pretexting the attacker impersonates people in certain roles that don’t have access to. For example, the attacker may impersonate amazons support team, law enforcement, etc. Like, “Hay, I am from the amazon support team, I am here to confirm your “X” order of $X, If you think it was a mistake, Please follow the steps to cancel the order (malicious steps). Or whatever, you got the idea.
OSINT And Social Engineering
OSINT is the technique of collecting information from publicly available sources on the internet. And you already know what social engineering is. OSINT is a part of social engineering. It’s the first step in the preparation for a social engineering attack. OSINT helps us to find valuable information about our target, then we can use the information to create a phishing mail.
Social Engineering Practical
Let’s see how you can create a phishing link using SET (Social Engineering toolkit). This tool comes by default installed in Kali Linux. For this example, we are going to show you only the technical part.
Our Objective: To get users’ credentials. For this, we will use a Twitter clone.
First run the set tool, by executing the `sudo setoolkit` command. Read the warning if you want, and accept to continue.
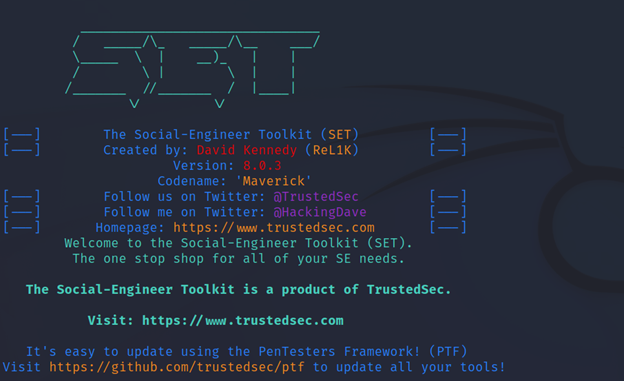
Now select 2 from the menu.
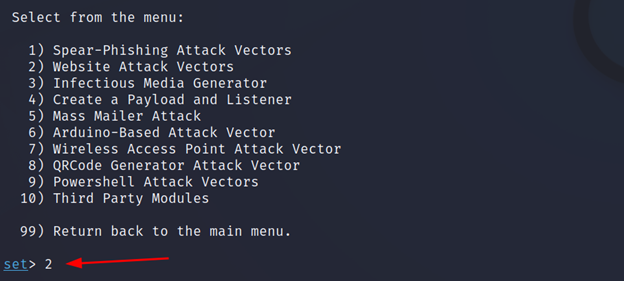
Now select 3 from the menu. Because we are going to harvest the credentials.
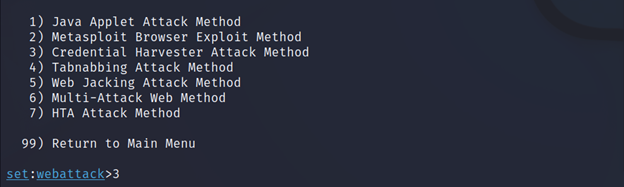
Now select 1, because it’s just a demo we will keep it simple.
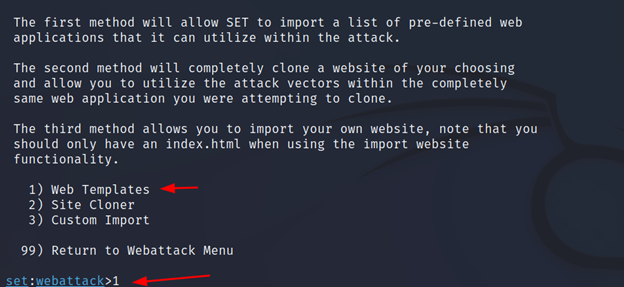
Now it will ask for the IP address, where the site will get hosted. Just click enter for the default.
Now select Template 3 Twitter.

Now the phishing site will be active on your given IP.
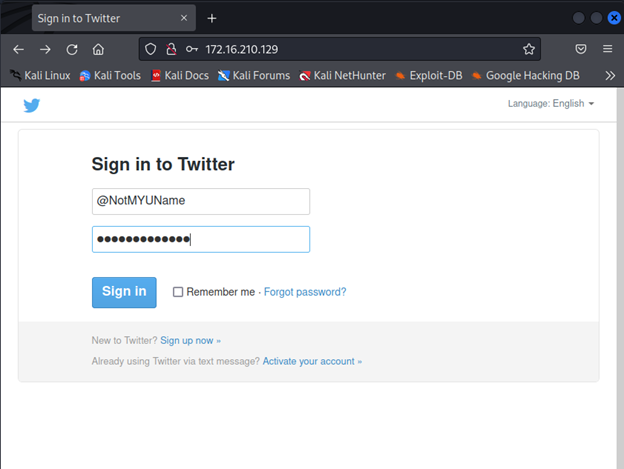
And you will be able to see a log-in page. Just fill in the information and hit “Sign In”.
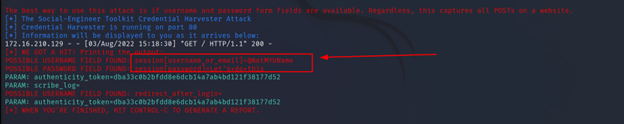
And when you do, you will be able to see the username, and password you’ve just entered. Just like this. And after that, it will redirect it to the original site.
There is so much that you can do with the SET tool. We recommend you try all of them. But do it in your system. Or we will not be responsible for any incident.
Now no one is going to fall for this trick. It looks like an obvious fake. Yes, it does, and the Twitter log-in page doesn’t match as well. And this is because we used a template.
Now why even do you have to try social media, you can try a different site that will be less suspicious by the victim. And about the IP, this is because we used our local host for the attack demonstration.
If you are going to do this in real life. You obviously have to buy hosting and domain name (similar to the target domain, with some minor changes that are less likely to be noticed when the victim is excited, feared, or emotional).
And how you are going to make them excited, by giving them an offer that they were looking for. For example, let’s see your target betting on an online site. And using osint you’ve found a tweet where he says, “It was my best move till now. Waiting for the result to be announced, Prize is $100k” or whatever you got the idea.
Then you can craft a phishing email saying that he won the first prize, with a phishing site(with a domain similar to the original). Now think when you send this email to the victim, (the victim already expects an email from the betting site) the victim will not check the domain name character by character. Probably he will have a look for less than a second. In this situation, the victim will do whatever you want. But it doesn’t mean everything, you should program the situation thoroughly before you plan any attack like this.
How to Avoid Social Engineering Traps
Now if you are looking for the ultimate way to prevent social engineering attacks. I am sorry to say, that there is no such thing. There is no 100% guarantee, all you can do is reduce the chances of attack.
And if you want to do that, you have to improve and check both the human part and the technical part.
Human Part
The best thing to do is train yourself or your employees through security awareness training. But you can follow a few tips. Such as
- Don’t click links, from emails that show the urgency of response. Most of them will be phishing links. For example, only the first 10 people will get the 90% discount. Or something like this. Here the attacker indicates that if you are not fast, you will lose the deal.
- Always check the domain when the site asks for any kinds of information to submit. What you can do is submit some fake information to check. Or best type the url yourself if the site is known like Facebook.
- Copy and paste the email that seems suspicious to google. There is a high chance that you will find out an article saying it is fake.
- Don’t just download and install any files. Always download files from trusted sources. For example, if the attacker says download our app for this offer. Don’t download it from the email, instead download it from the play store. This way you will recognize that it’s fake.
- Don’t purchase anything from any given link by email/SMS/etc. Purchase what you want directly from the official site. I know there are genuine emails as well. But you may create a habit of this. So better be safe.
- Now don’t fall for greed. For example, you have an email saying the emailer will send you 30% money if you receive 100k from him and send it to another address. Or whatever that shows you a big sum of money.
- Don’t fall for any emotional story. For example, you might get an email saying that the emailer has a tragedy, someone died, blah blah, and asking for your help. These types of messages are 100% fake.
One real-life example is this message. “I’m writing this message from the hospital where I’ve been treating as brain cancer patient,
Meanwhile, I am a widow so have decided to use my inherited fund in building of large Orphanage Homes there with your help. Your cooperation will be appreciate, here is my email ID for more details ([email protected])“
You can check more examples out here.
I received this message from a fake ID of a woman. Now if you feel pity for the woman and email her. You will fall right into the attacker’s trap.
Technical Part
Keep your system up to date. This way attacker wouldnt be able to abuse any vulnerability unless it’s zero-day.
Social engineering is mostly dependent on the human part. So, there is not much you can do technically. As I already said no matter how perfect security defense you use. It will fall before a human error.
There is a great quote about this,
Social engineering bypasses all technologies, including firewalls.
Kevin Mitnick
Final Words
There is more action you can take to avoid social engineering. But whether you can save yourself or not depends on if you are a specific selected target, or mass selected target. If you are mass-selected, for example, the attacker has 1000 emails and you are one of them, you are less likely to fall for the trap. But if you are selected individually, there is a very high chance that you may fall victim to the attack. So, be alert! be safe!

