In cyber security reconnaissance (recon) is a process of collecting information about the target. The target could be an individual or corporation. In recon, we gather information for both the user(human) and the system (computer). In this process, we collect as much data as we can about the target such as Information about their system, users, services, versions, etc.
It’s the first step in ethical hacking and penetration testing, after getting approval from the client. A penetration testing success highly depends on these information-gathering steps.
Types Of Reconnaissance
The complete process of reconnaissance is divided into two parts. They are passive recon and active recon. Let’s have a look at them.
Passive
This is the process where we collect information about the target without directly connecting to the target. In this process, we use third-party tools, links, and services to get our objectives. For example, when we gather information about a user/system we don’t connect to the target’s system directly. We connect to google and google connects to the target’s system. In this process, google serves as a proxy for us.
Google was just an example, but there are tons of other ways of getting information passively. And there is no limit to how much information you can gather about the target. Let’s look at this practically.
Google Hacking
Google Hacking or Google Dorking is the process of using Google advanced filtering keywords to filter a search result from billions of results. This is so much useful that sometimes with just google dorking you can find critical vulnerabilities to compromise the target’s system. And since google automatically gathers all the information. This becomes a great source of collecting information. It’s also a part of OSINT.
Let’s look at some examples:
site: Using this you can find the content of a specific site.
Example site:google.com “hello”
intitle: This will show all the pages that have the “string you used” in their HTML title tag. Example: intitle:”Hello World”
inurl: It searches for specific strings in the URL.
Example inurl:login.php
filetype: Searches for the specific file type.
Example filetype:pdf “hello”
ext: it works similar to filetype.
intext: This will search the whole web page’s content for the specified text and if found it will show in the search result.
cache: This will show the cached version of the searched website. Example: cache:google.com
*: This is a wildcard that works like a regular expression. Example: Hello Wo*ld, will show the result of “Hello World, Hello Woald and all the combinations that regular expression finds.
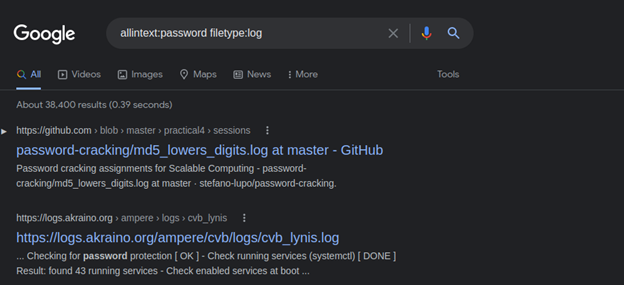
Log Files for login credentials
This dork will search for .log files which are exposed on the internet. This is basically a log file that contains clues about what the credentials to the system might be.
allintext:password filetype:log
Credential hunting in ENV file
.env (environment) file is used by various popular web development frameworks to declare general variables and configurations for local and dev environments.
DB_USERNAME filetype:env
DB_PASSWORD filetype:env
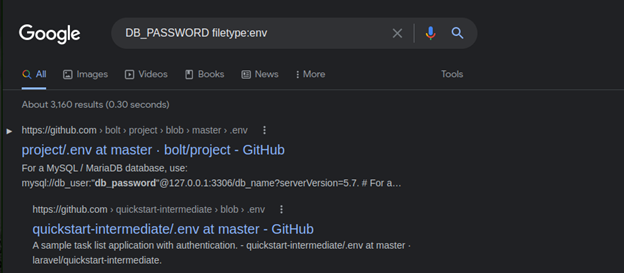
Using this dork you will find a list of sites that exposed their env file on google search.
Note: This dorking is shown just for educational purposes, we won’t be responsible if you use it for evil things. And if you want to gather info about a specific target also use the site keyword with other keywords.
Wayback Machine
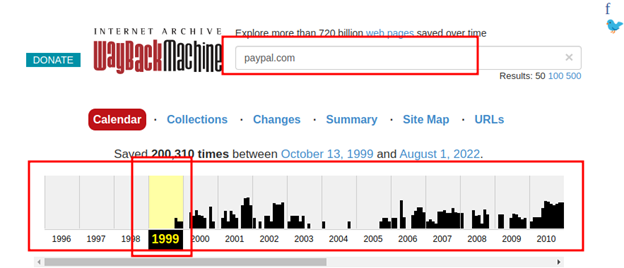
Simply put it’s an archive of the internet. Using this online tool you can go back in time. This helps you to find confidential information about the target. You can also archive any site url in the Wayback machine. Let’s see what PayPal looked like back in time.
Search your target url in the search bar. Manage the timeline of archives.
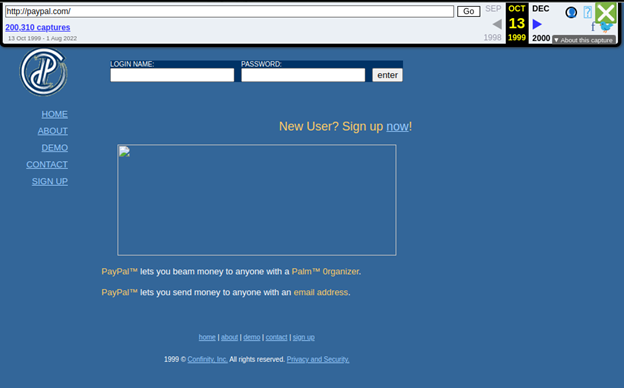
Click on the snapshot you want to see.

Whois
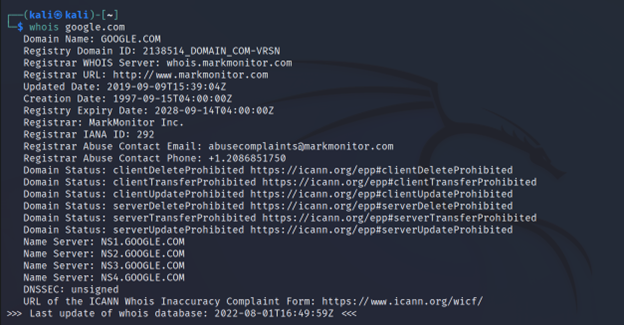
Whois is a simple request/response protocol that listens on TCP port 43. It is used to store the registered user’s domain name and other info. When someone registers a domain name, the registrar collects some data about the domain registrant. Using whois we can get so much information, such as
- Domain registrar name
- Registrant Contact info: Name, org, address, phone, and more. (The domain owner can hide this using a privacy service provided by the registrar)
- Domain Creation, expiration dates
- Name Server and more
Let’s see it in action.
Try other domains, the result will be more interesting. Due to DMCA we just cannot pick any domain address. So, we have limitations here.
DNSDumpster
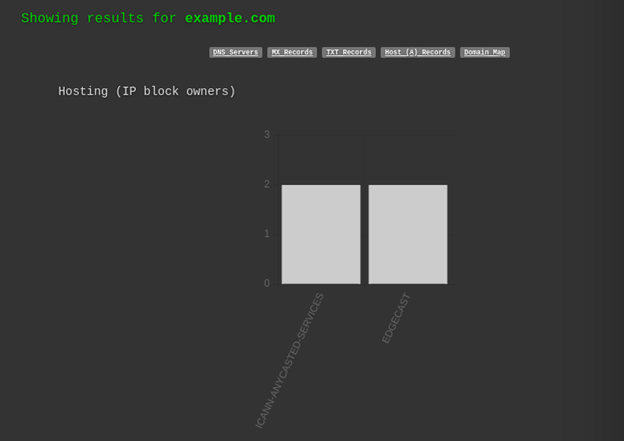
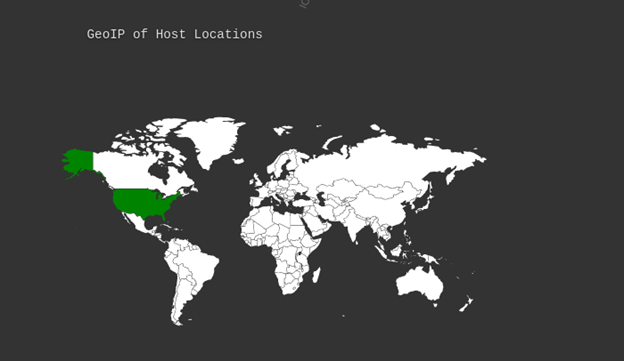
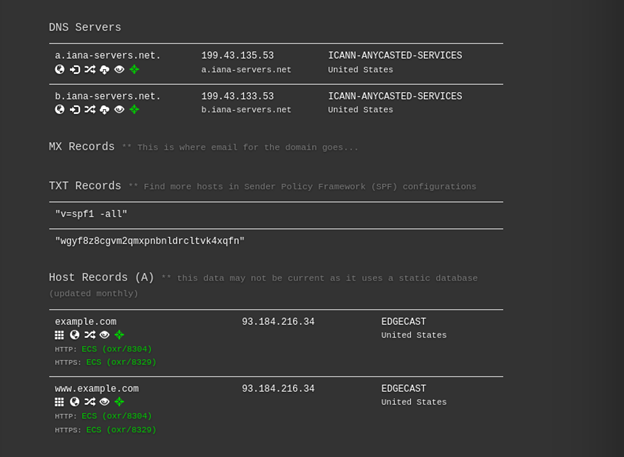
DNSDumpster is a DNS dumping utility. Using it you can find the subdomains of the target. It gives you data in a visual form. You can check the hostings, GEO locations of hosts, DNS Servers, MX Records, TXT Records, Host Records, IP addresses, subdomains, etc. Not just that you will also get a domain mapping image, xlsx of hosts, and a view graph mode.
Here we are showing an example of the example.com domain.
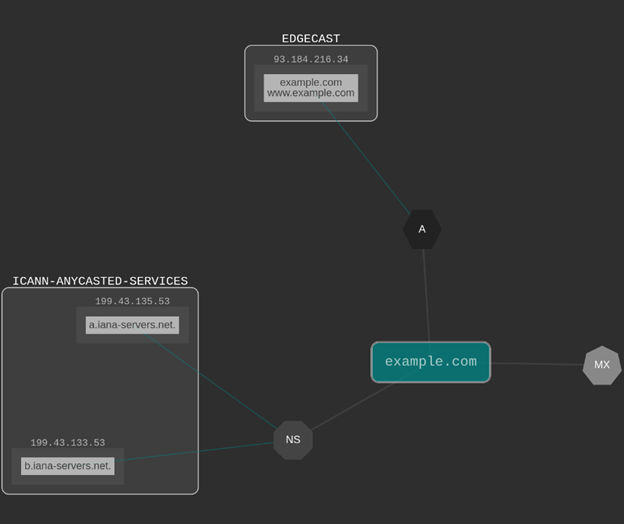
Graph View
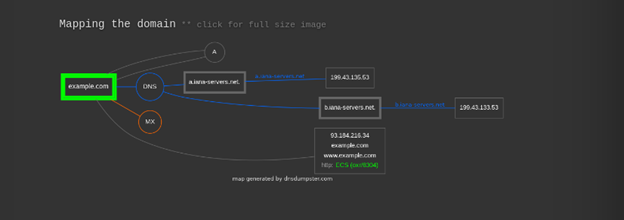
Domain Mapping
Try different domains, For example, try google. And you will be able to see more.
Shodan.io
Shodan is a very powerful search engine for IoT devices. Using shodan you can learn about target systems’ open ports, services, versions, location of hosting, IP address, specific vulnerabilities, and much more.
Search your target domain/IP in the search bar.
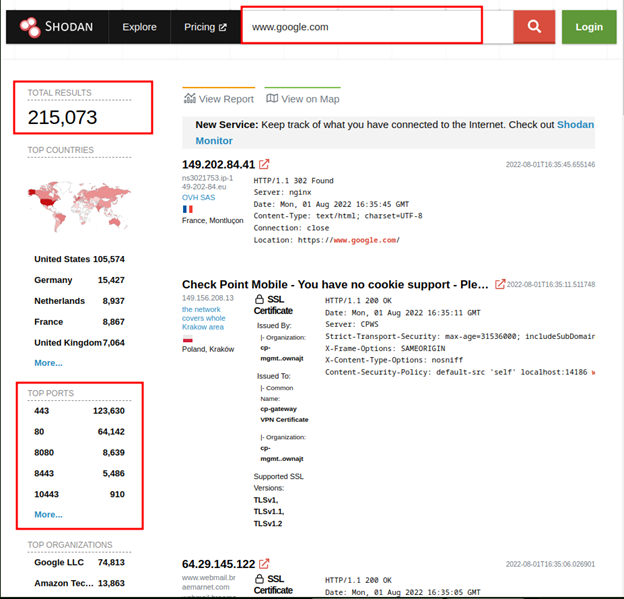
Click on your target, you’ll be able to see more info.
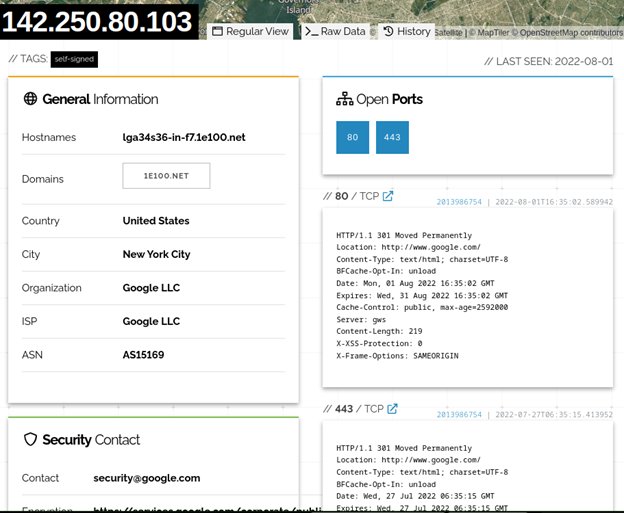
You can also search via software name or version. This way you can target a vulnerable version and check if your target is vulnerable or not.
Note: Here we will not talk about random hacking. All our articles will be target based. And our target will be predefined.
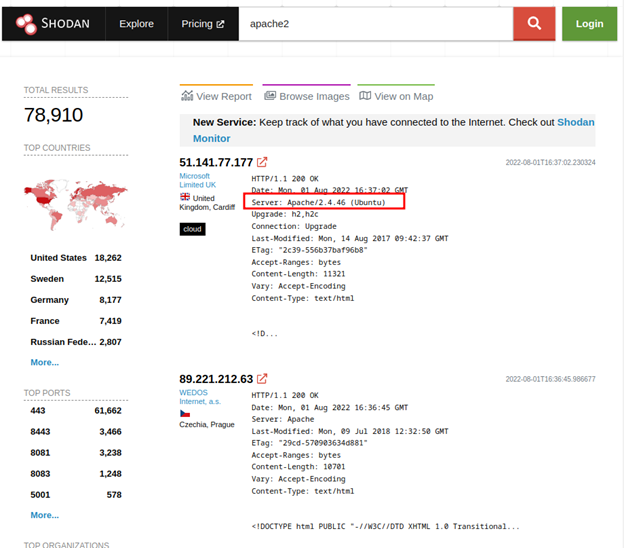
There is so much into shodan. Some of them require a premium plan, and some of them can’t be shown because of policies. Check this to know more uses about shodan. Check the ADB and use the ghost framework to exploit it, you will be surprised.
Active
Active reconnaissance is the complete opposite of passive reconnaissance. In Active recon, we directly connect to the target’s system and extract information from there. In active recon, we get more accurate information about the target. Like what ports are open, what services are running, their version, and more. This gives us a good amount of information to map the target’s system/network.
But unlike passive recon where the target doesn’t get to know about us. It’s the opposite in active recon. Here our every request creates a log in the victim’s machine, telling them that someone is trying to penetrate inside. This also becomes a problem when there is a firewall activated. So, when doing active recon we should be as silent as possible to avoid possible detection by the defense system/security team.
Each of them has its own advantage. And both are necessary for penetration testing.
Let’s see some of the methods of active recon.
Ping
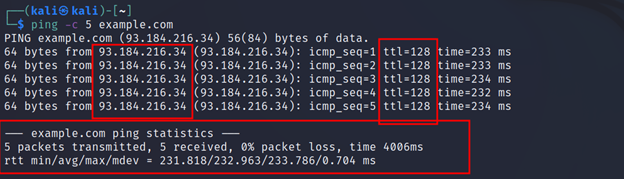
Ping is the most basic network command. It is used to check whether a host is alive or not. Ping uses ICMP packets to check for alive hosts. You can also see the target’s IP address using the ping command. You can also see the TTL value, which can be used to identify the target’s os. You can check this out here.
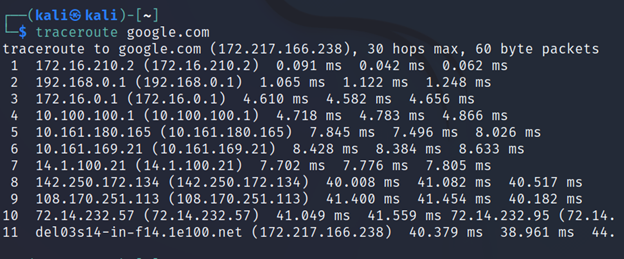
Traceroute
Traceroute is used to trace packet routes from your machine to the target machine. For example when you connect to google your pc requests that to your home router, from that to your isp’s router, and so on.
Nmap
Nmap is a real deal here unlike ping, or traceroute. You can do both in Nmap. It stands for Network mapper (Nmap), using Nmap you can perform port scans on your target’s IP. And from there you can also detect the services and versions running on that port. Not just that Nmap has a scripting engine that you can use to directly scan for vulnerabilities. Let’s look at some basics of Nmap.
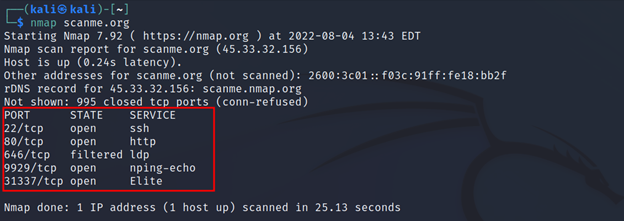
For a normal scan, you can simply run Nmap with the target’s IP.
Command Executed: `nmap <IP>`
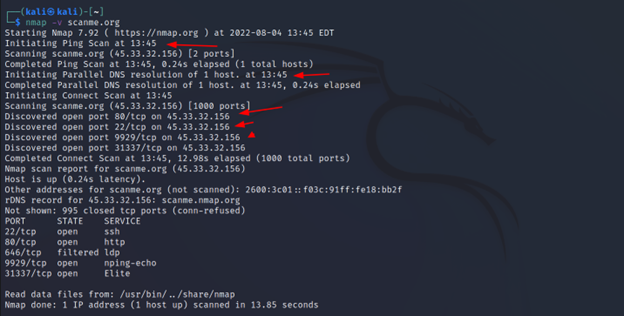
If you want to know what’s going on on the run. You have to enable the `-v` switch. You can also press “v” if you forget to add the switch. There’s no need to rerun the scan.
Command Executed: `nmap -v <IP>`
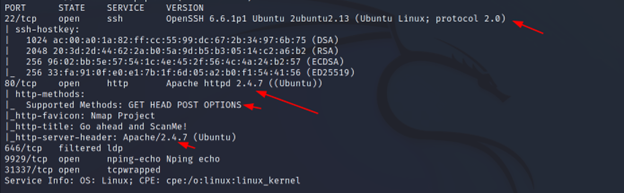
This will scan for the first 1000 ports, and scan for service, and version. Also, run traceroute, and scan for vulnerabilities with NSE (Nmap scripting engine).
Command Executed: `nmap -A -v <IP>`
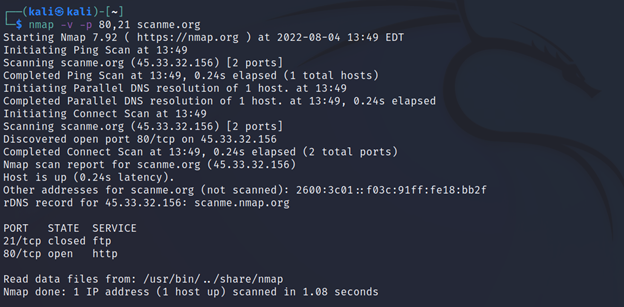
Command Executed: `nmap -v -p 80,21 <IP>`
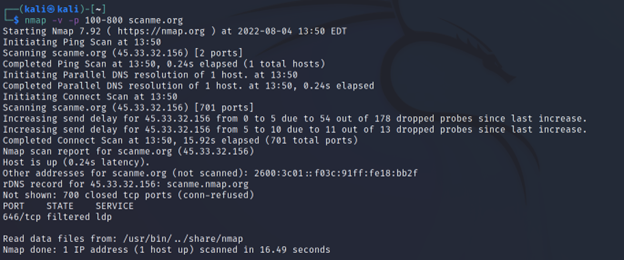
Command Executed: `nmap -v -p 100-800 <IP>`
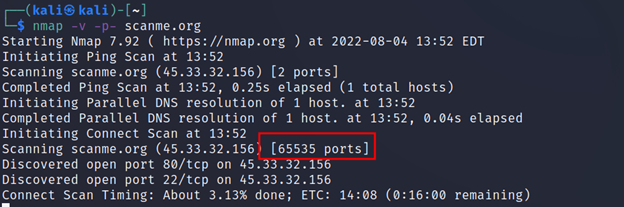
For scanning all the ports. This will take a lot of time.
Command Executed: `nmap -v -p- <IP>`
There are so many commands and uses of Nmap. You have to learn it by yourself till we release an article specifically about Nmap. You can take help from the help menu and google/Nmap official docs.
Subdomain (active)
Usually, you will receive one single domain for your pentest project. But there could be more subdomains, finding subdomains will make the scope better. It will enable you to look out for more information. A target’s main domain is secure doesn’t mean the rest subdomains will be secure too. Let’s see how you can find subdomains.
We are going to use a tool named sublist3r. This tool is by default installed in all the hacking distros. Like Kali Linux, parrot sec, etc.
In case you don’t have it. You can install it by executing the below command.
Command Executed: `sudo apt install sublist3r`
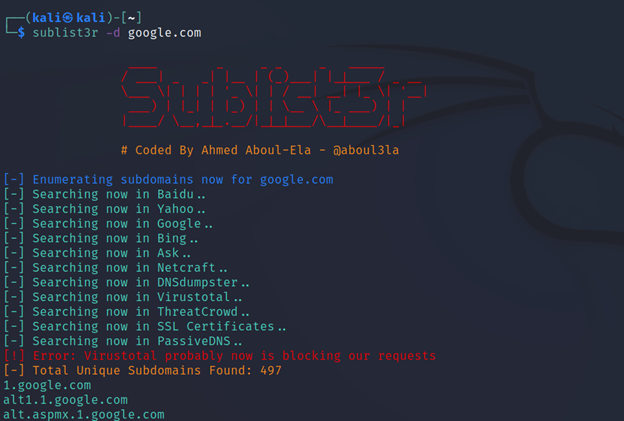
And that’s how you search for subdomains in sublist3r.
Note: Sublist3r can be used for both passive/active gathering.
Command Executed: `sublist3r -d google.com`
Directory fuzzing (active)
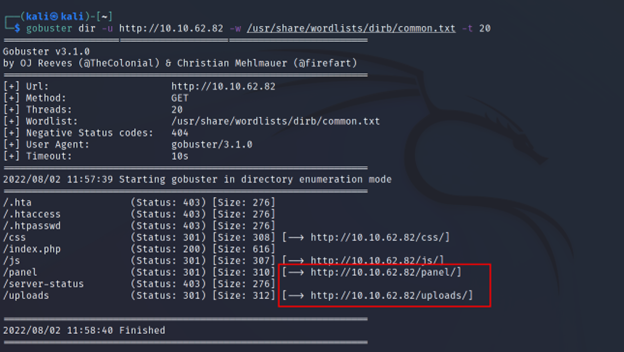
There are directories that you won’t see on site. They are the hidden directories. Those directories sometimes contain API Keys and much secret info. This could be an easy win. Not just that you can also discover new websites in a different directory. For this, we are going to use a tool called gobuster.
This tool is written in go lang, it brute forces directory from a word list given by the user. Let’s see how we can use it.
Command Executed: `gobuster dir -u http://10.10.62.82 -w /usr/share/wordlists/dirb/common.txt -t 20`
Final Words
There is so much to reconnaissance. Even if we write about it for months, it wouldn’t be enough to cover everything. But those were the basics and most essential techniques. The rest depends on you. Keep learning, keep practicing, till the next article is ready.

