What Are The Different Mobile App Testing Tool?
Introduction Users expect their mobile applications to be more usable, secure, and high-quality due to the industry’s intense competition. Mobile app assessment makes it easier to identify flaws in an

Introduction Users expect their mobile applications to be more usable, secure, and high-quality due to the industry’s intense competition. Mobile app assessment makes it easier to identify flaws in an

Introduction Although it’s necessary to maintain your business safety, software and network Limitations of Vulnerability Scanning services are not a complete solution. This will assist you in finding system vulnerabilities—new
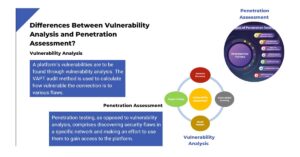
Introduction Absolutely guarantee that Differences Between Vulnerability Analysis and Penetration Assessment is only meant to catch your eye. They are not, in that way, adversaries. In actuality, the appraisal of
Introduction Every day, the risk posed by hackers becomes more severe. Well over 450 IT intelligence officials participated in a Technical Republic study, and the results showed that 71 percent

Introduction We offer IT emulation sincere thanks for introducing us all to cloud computing. Today’s IT systems already use virtual servers to execute mission-critical enterprise applications. Cybersecurity issues affect virtualization

Introduction Do you frequently shut off applications on your Android device? This isn’t quite as useful as you could believe. This is the reason. Many individuals believe that regularly logging

Introduction A pen-goal test is to increase your company’s risk resilience so that you may track, monitor, and mitigate breaches while also lowering their effect on your company. VAPT solution service

Introduction Information loss prevention equipment is quickly emerging as a critical IT protective strategy in an era of strict data privacy regulations, such as GDPR but also CCPA. Each business

Introduction Cyberattacks are increasingly becoming more widespread and destructive over time Because of this, government agencies and worldwide technical standards work to control cybersecurity by implementing more stringent cybersecurity compliance

Introduction A Mobile application is initially given no permissions by definition. The user must grant consent whenever the program wants to employ a portion of the device’s limited capabilities (such