What is Caldera?
Caldera is a cyber security platform designed to easily automate adversary emulation, assist manual red-teams, and automate incident response. It’s based on the MITRE ATT&CK Framework.
The framework consists of two components:
- The core system. This is the framework code, consisting of what is available in this repository. Included is an asynchronous command-and-control (C2) server with a REST API and a web interface.
- Plugins. These repositories expand the core framework capabilities and providing additional functionality. Examples include agents, reporting, collections of TTPs and more.
System Requirements:
These requirements are for the computer running the core framework:
- Any Linux or MacOS
- Python 3.7+ (with Pip3)
- Recommended hardware to run on is 8GB+ RAM and 2+ CPUs
- Recommended: GoLang 1.17+ to dynamically compile GoLang-based agents.
Installation:
The installation process is simple, first we need to make sure that we have the required dependencies after that, clone the git repository by running:
git clone https://github.com/mitre/caldera.git –recursive


Next, move to the folder where the repository is cloned, this can be done by:
cd caldera

Install using pip3 by running the below command:
pip3 install -r requirements.txt
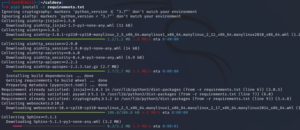
Finally, start the server using the below command:
python3 server.py –insecure
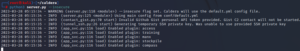
It will create a listener on port 8022 and server on port 8888
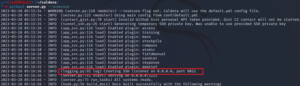
Open your browser and go to 127.0.0.1:8888, Caldera Web interface will be shown
Username: red
Password: admin

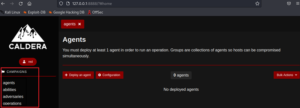
The Interface will look as shown below:

The interface is broken into 4 sections:
- Agents
- Abilities
- Adversaries
- Operations
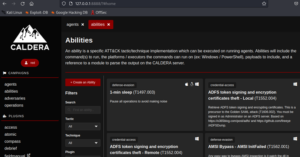
Abilities
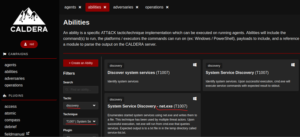
An ability is a specific ATT&CK tactic/technique implementation which can be executed on running agents. Abilities will include the command(s) to run, the platforms / executors the commands can run on (ex: Windows / PowerShell), payloads to include, and a reference to a module to parse the output on the CALDERA server.
Adversaries
The Adversary section helps cyber teams for emulating specific types of adversaries to test their systems against specific threats and tactics.

Operations
Operations run abilities on agent groups. Adversary profiles are used to determine which abilities will be run and agent groups are used to determine which agents the abilities will be run on.

Plugins
The plugins section contains all the plugins which come along with Caldera and any others which you might wish to install.
The components under campaign (agents, abilities, adversaries and operations) are used to create and drive a campaign used by red teams for adversary emulation.
Adversary emulation is a type of red team engagement that mimics a known threat to an organization by blending in threat intelligence to define what actions and behaviours the red team uses. This is what makes adversary emulation different from penetration testing and other forms of red teaming. Adversary emulators construct a scenario to test certain aspects of an adversary’s tactics, techniques, and procedures (TTPs). The red team then follows the scenario while operating on a target network in order to test how defences might fare against the emulated adversary.
Let’s check out how we can perform adversary emulation in real time.
First, we need a target machine. For testing purposes, we will use a machine owned by us. Please do not try and attempt this on someone else’s computer without prior permission. We would also need enough privileges on that system to install software.
We are assuming that you have access to target machine with installation permissions.
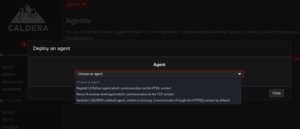
Deploy the agent on the target machine starts with choosing an agent. There are three options.
We are choosing Manx which is a reverse shell via TCP connect.
Platform : For Windows
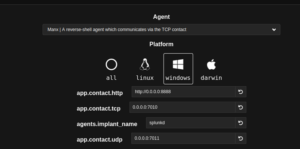
Scroll down and you will find the commands which need to be executed on the target machine.

Here replace 0.0.0.0 with the server ip which has Caldera Installed.
Copy the code and execute it on the target machine via power shell (since we have selected windows operating system).
On Target Machine, we have opened powershell:
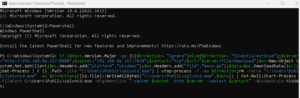
Copy paste the code into it:
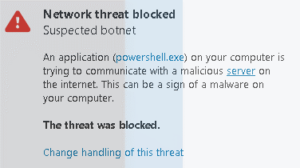
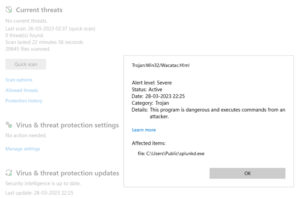
If target machine has any network threat detection mechanism, this code run will be detected immediately
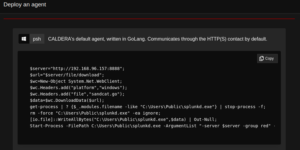
As we are getting an error in this type of agent, we are choosing Caldera’s default agent.

Copy the code
![]()
You may have to give it permission
Note: This technical blog is only to demonstrate the step by step process of running campaigns via caldera. In reality you will face a lot of challenges as end point protection agents tend to block the PS script or any other suspicious program. Though there are methods to evade them also, but those tactics are beyond the scope of this blog.
Once the command is successfully executed on target machine, it will reflect under agents tab in caldera.
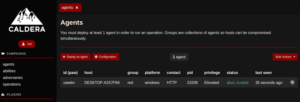
The First Step is over. Now we have to move on to second step which is Configuring the abilities.
An ability is a specific ATT&CK tactic/technique implementation which can be executed on running agents. Abilities will include the command(s) to run, the platforms / executors the commands can run on (ex: Windows / PowerShell), payloads to include, and a reference to a module to parse the output on the CALDERA server.
We have selected defense evasion ability with technique as “Grant Full Access to Folder to Everyone”
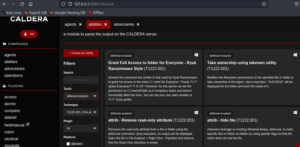
Create Adversary

Create Operation and Run

The commands are encoded

Another Example:
For Discovery
Creating Ability
Creating Operation
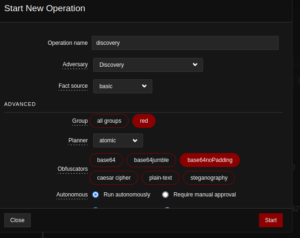
Operation Output
First it hunted the local users and then associated user processes as defined above in Abilities
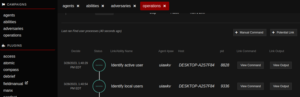
Userlist output

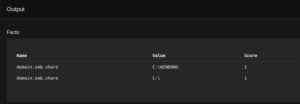
Identification of admin shares, domain, AV, Groups and FW
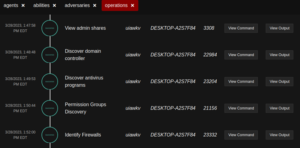
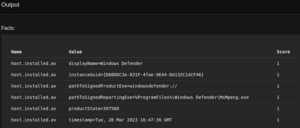
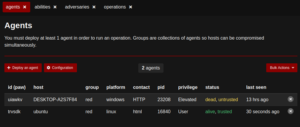
Similarly we can create an agent for Linux machine.
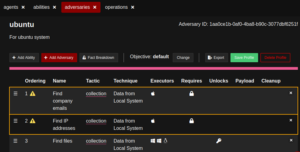
Create one collection ability for agent

And run operation

For example: Under this current operation our task was to create a directory named as stage on target machine
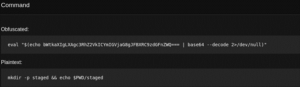
We observed one folder with same name was created on target machine under root folder

It got permissions: drwxr-xr-x , which has read, write and execute permissions for the owner, but only read and execute permissions for the group and for other users on target machine.
With this, the blog comes to an end. Caldera is a very extensive tool based on the MITRE ATT&CK Framework and should be in the toolkit of any red teamer to aid them in their adversary emulation exercises.

